Transport Layer Security
Contents
What is Transport Layer Security?
Transport layer security is a cryptographic protocol that's designed to provide secure communication over computer networks. TLS ensures that hackers cannot breach your data privacy. This protocol is commonly used to protect such things as passwords, personal correspondence, emails, and credit card numbers, among others.
How TLS works
TLS comes from Social Socket Layer (SSL) which Netscape Communications Corporation designed in 1994. It combines the handshake protocol and record protocol.[1] While the handshake protocol is used to validate the communication participants, the record protocol is used to ensure the credibility of the data exchange.
At the point of creation, the aim of TLS was to keep web sessions safe through efficient security. There were three versions of SSL before TLS emerged. SSL 1.0 was never made public while SSL 2.0 was swiftly replaced with SSL 3.0. The 3.0 version formed the basis of TLS.
TLS is a protocol that uses cryptography to provide air-tight security. Using both asymmetric and symmetric cryptography, this form of security has high performance, and efficiently protects data. Symmetric cryptography requires the use of a private key to encrypt data. Both the data sender and the receiver know the encryption key. Regarding computation, the symmetric method is very super-efficient.
However, it is noteworthy that the secret key must be shared through a secure channel so as not to compromise it. The key has to be 128 bits in length. Preferably, it should be 256 in length. Keys that fall below 80 are now generally considered insecure for processes.
On the other hand, asymmetric cryptography makes use of key pairs. This means that there are two key forms during the encryption and decryption stage. These are the public and private keys. Even though one of the keys is public, it is impossible to extract the private key through the public one due to the tight security. This ensures that the TLS protocol remains safe, and nothing compromises the data security.
TLS also makes use of larger sizes of keys, with bits running between 1024 and 2048. This makes it an intensive protocol with adequate security.
Key generation methods
The TLS protocol uses any of the various key generation methods such as Ephemeral Elliptic Curve Diffie-Hellman (ECDHE).[2] These methods offer secure channels to ensure the keys' safety even if a key gets obtained in the future by a third party.
It is noteworthy that weak keys or keys containing a deficiency in prime numbers have been seen to be susceptible to being compromised. However, this is an implementation problem and not essentially a protocol issue. Tools exist for determining the strength of these numbers.
For the transport security layer protocol, it is essential that the client that joins the server can validate the server's public key. That process is usually conducted through the use of an X.509 online certificate. This certificate is provided by a credible 3rd party referred to as the Certificate Authority or CA.
The purpose of the CA is to validate the public key's originality. Alternatively, a server might employ the use of a self-issued certificate to serve the security needs. Irrespective, if a website is secure, the browser will display such with a padlock icon as shown in the screenshot below.
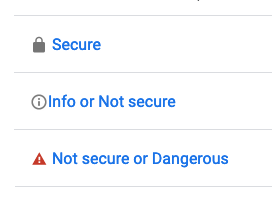
Screenshot of google.com indicating the meaning of security symbols
What is the difference between TLS and SSL?
TLS evolved from Secure Socket layer (SSL). The operation of the two models is different. TLS evolved as a stronger protocol that affords a more efficient data exchange. Over the years, TLS has become a popular method in use. But it is crucial to understand what TLS is doing that SSL couldn't do.
The essential difference between the TLS and SSL has to do with the cipher suites.[3] The cipher suite is the algorithm that deals with key generation, encryption, transfer, and other algorithmic processes with the key. Each TLS or SSL version has its unique cipher suite, and it keeps improving with each model.
More modern apps are embracing TLS as against SSL. Most apps do not support SSL 3.0 anymore. Case in point is Google Chrome that stopped SSL as far back as 2014.
Importance of TLS for SEO
TLS is critical to your website’s ranking because it offers more levels of protection. Using HTTPs is directly responsible for your website's ranking. However, while HTTPs offers protection for users on your page, it is not comprehensive enough for instances where they share precious information like credit card details.
Therefore, for that purpose, you need to install TLS. In a nutshell, having TLS for your website addresses the security and risk concerns you may have and promotes user confidence.
References
- ↑ [1] Science Direct. 4 February 2021.
- ↑ [2] ECHDE. Retrieved 4 February 2021.
- ↑ [3] JSCAPE. Retrieved date.
https://www.internetsociety.org/deploy360/tls/basics/
https://www.jscape.com/blog/cipher-suites