Hashing
Contents
Hashing definition
Hashing is the process of creating a digital signature for a document or string of text. This signature is called a hash and can be used by the receiving party to verify that a form, data, or line of text is unchanged.
Hashing can be used to check whether important documents, including software files and legal documents, are unedited and come from the right source. Hashing is also commonly used for storing passwords, although other supporting methods are widely used alongside it to improve security.
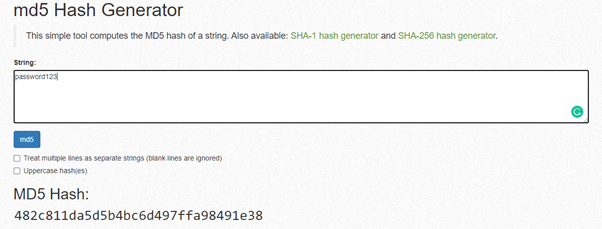
An example of the hash created by the MD5 hashing function when “password123” is inserted on MiracleSalad.
How hashing works
Hashing works by turning written data into a seemingly random string of characters. It uses a hashing function, which is a type of algorithm that follows set rules for altering the original characters into a unique hash value that’s very different from the original.
The string of characters generated through hashing is called a signature, value, or hash. It should be unique and should change completely if any minor edits are made to the original text.
What is hashing used for?
Hashing is commonly used for verification, including the verification of documents, data, and files. By checking the hash of downloaded files, a user can be sure that the file is unedited and came from the original publisher. This helps prevent the spread of malware and prevents security issues.
Hashing is also used for storing passwords. Instead of storing the actual password, the hash value is stored on the backend. If a hacker gets access to the database, they only have access to the hash and not the actual passwords.
While hashing does help improve password security, other supporting steps are required to ensure the security of passwords.
Hashing best practices
There are a number of best practices that are important to follow when hashing, a few of which are listed below:
- It shouldn’t be too fast
Although it shouldn’t take long to execute a hashing function, it’s important the hashing function isn’t too fast. This can indicate that it’s easy to crack.
- Small changes to the original document or text should result in major changes to the hash value. It’s vital that any minor changes made to the original data generate a completely unique hash.
- Salting
Salting is the practice of adding characters to the data before hashing. Since brute-force attacks can still be used to crack hashed passwords, adding characters to the original data can prevent previously cracked passwords from being shared with other hackers.
The difference between hashing and encryption
Hashing and encryption are often confused with one another, but there’s one major difference between the two. Namely, hashing only works one way, whereas encryption works two ways.
After data has been hashed, the value created can only be used to verify the original data or document. It does not allow you to see what the password or document said. With encryption, the entire file is preserved and can be recovered by the receiving party using the encryption key. This means that it can be used to send and receive messages and data securely, unlike hashing.
Examples of hashing algorithms
- MD5 – The MD5 hashing function is an older function that isn’t used much anymore due to it being less secure than more advanced hashing functions.
- SHA-1 – SHA-1 is also considered as a less-secure hashing method, generally resulting in a short hash value when compared to more advanced functions.
- SHA-3 – SHA-3 is a more secure hashing function that is more commonly recommended today.
Importance for web development
Hashing is an important part of developing secure websites and web applications, ensuring a good user experience. By understanding how hashing works and implementing best practices, you can provide your users with improved security.
Related links
- https://www.thesslstore.com/blog/difference-encryption-hashing-salting/
- https://auth0.com/blog/hashing-passwords-one-way-road-to-security/
| About the author |
 |